SOC 2 doesn’t require you to slow down your CI/CD pipeline—it requires you to prove it’s secure. In this guide, we break down how to embed SOC 2 controls directly into your cloud-native CI/CD workflow, including change management, access controls, automated security testing, and audit-ready evidence collection. If you’re moving from DevOps to DevSecOps and preparing for SOC 2, this article shows how to turn your pipeline into a continuous compliance engine without sacrificing velocity.
Canadian Cyber • SOC 2 • DevSecOps
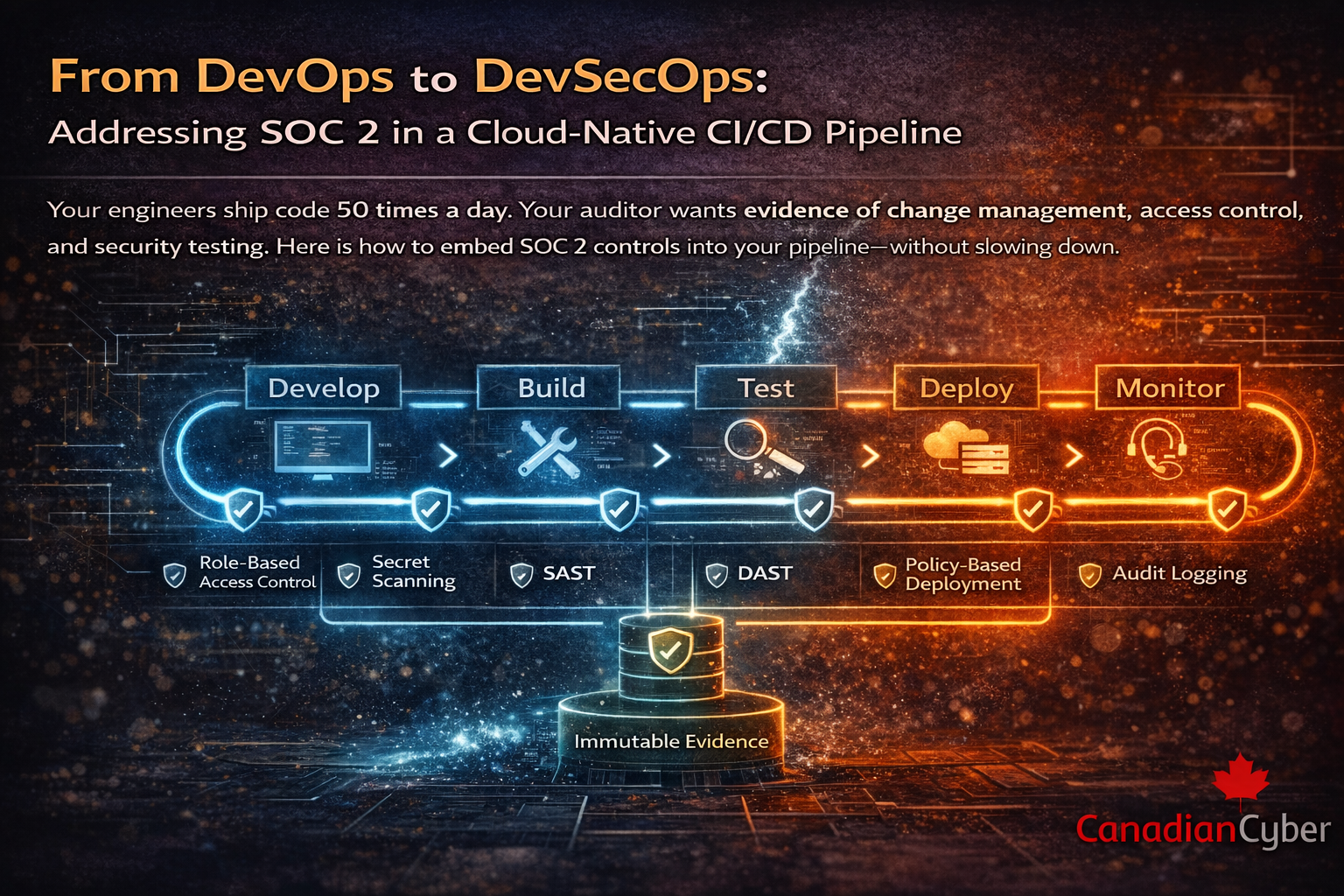
Your engineers ship code 50 times a day. Your auditor wants evidence of change management, access control, and security testing.
Here is how to embed SOC 2 controls into your pipeline without slowing down.
Your team ships code 30, 50, sometimes 100 times a day. PRs merge in minutes. Containers deploy automatically.
Then SOC 2 arrives and the auditor asks:
DevOps optimizes for velocity. SOC 2 optimizes for verifiability. Done right, SOC 2 becomes automated guardrails that improve reliability not red tape.
SOC 2 doesn’t care about your tools. It cares about outcomes and evidence. These criteria typically touch CI/CD:
| SOC 2 Criterion | What It Means for Your Pipeline |
|---|---|
| CC6: Logical Access Controls | Who can push, approve, and deploy to production? |
| CC7: System Operations | Monitoring, anomaly detection, security event response |
| CC8: Change Management | Authorized, tested, approved changes before prod |
| CC4: Monitoring Activities | Immutable logs and traceability: prove what happened |
Requirement (CC6): production environments must be configured securely and consistently.
The DevSecOps approach: everything is code, reviewed, and scanned.
| Practice | Tool Examples | What It Proves |
|---|---|---|
| IaC scanning pre-merge | Checkov, tfsec, Terrascan | Misconfigs caught before deployment |
| Policy as Code | OPA / Gatekeeper | Rules enforced programmatically |
| Immutable infrastructure | Terraform, Bicep, CloudFormation | Consistent, repeatable environments |
Requirement (CC6): access to pipelines and production systems must be restricted and logged.
Build RBAC + MFA + immutable audit logs.
| Control | Implementation |
|---|---|
| Branch protection rules | Require PR reviews, status checks, linear history |
| Least privilege for CI/CD | Service accounts with minimum permissions |
| MFA everywhere | Enforced via GitHub/GitLab/IdP |
| Audit logging | Pipeline actions logged and streamed to SIEM |
Requirement (CC7): detect and address vulnerabilities. Replace annual “hope” with per-commit feedback.
| Test Type | What It Finds | When to Run |
|---|---|---|
| SAST | Bugs in custom code | Every PR |
| SCA | Vulnerable dependencies | Every PR + daily |
| Container scanning | Vulnerable base images | On build + daily |
| Secret detection | Hardcoded credentials | Every commit |
| DAST | Runtime vulnerabilities | Staging |
Requirement (CC8): changes must be authorized, tested, and approved before production.
Embed change management into your PR workflow.
| Change Control Element | How CI/CD Handles It |
|---|---|
| Authorization | PR approval from designated reviewers |
| Testing | Automated tests must pass |
| Documentation | PR description + linked ticket |
| Segregation of duties | No self-approve + merge for critical changes |
| Emergency changes | Documented override + post-incident review |
Requirement (CC4): retain monitoring and evidence. Move from “screenshot season” to continuous collection.
| Evidence Type | Source | Retention |
|---|---|---|
| PR approvals | GitHub / GitLab API | Audit cycle + 1 year |
| CI/CD logs | Build system | 1 year, immutable |
| Scan reports | Security tools | 1 year, immutable |
| Deployment logs | CD system | 1 year, immutable |
| Access logs | Identity provider | 1 year, immutable |
Fragmentation is the enemy of compliance. If scans, access logs, and deploy records live in different places, audit prep turns into archaeology.
The fix is a unified control layer: control → data source → evidence → immutable storage.
┌───────────────────────────────────────────────┐ │ SOC 2 CONTROL MATRIX │ ├─────────────────────────┬─────────────────────┤ │ CC6 Access Controls │ Git roles, MFA, logs│ │ CC7 Operations │ Alerts, scans, IR │ │ CC8 Change Management │ PR approvals, tests │ │ CC4 Monitoring │ Immutable evidence │ └─────────────────────────┴─────────────────────┘
We’ll review your branch protections, CI/CD identities, scanning gates, and log retention and tell you what will pass SOC 2 without slowing shipping.
| Gap | Why It Happens | The Fix |
|---|---|---|
| Overprivileged CI/CD credentials | Service accounts accumulate permissions | OIDC federation, least privilege, quarterly reviews |
| No audit logs for pipeline actions | “We trust our team” | Enable audit logging; stream to SIEM |
| Manual emergency changes | “We had to fix it fast” | Document overrides + post-mortems |
| Inconsistent IaC scanning | Some repos opt out | Org-level enforcement + required status checks |
| No segregation of duties | Same person approves and merges | Branch protection + CODEOWNERS for critical paths |
| Level | Description | Audit Outcome |
|---|---|---|
| 1. Ad-hoc | Direct prod changes, no scans, no logs | Critical findings |
| 2. Defined | CI/CD exists; evidence is manual (screenshots) | Major findings |
| 3. Automated | Scans in CI; access controls; logs collected | Minor findings |
| 4. Continuous | Evidence auto-collected; controls mapped to pipeline | Clean opinion |
| 5. Predictive | Anomaly detection + automated remediation + improvement loops | Competitive advantage |
DevOps was built to eliminate friction. SOC 2 was built to ensure accountability. They are not enemies.
This is DevSecOps. This is continuous compliance. Your engineers keep shipping. Your auditors keep verifying.
And compliance stops being “separate” from how you build software—because it never was.
We’ll review your CI/CD configuration, access controls, scan gates, and evidence retention and tell you what to automate first for maximum SOC 2 impact.