ISO 27001 Control 5.30 ensures that development and testing don’t compromise production. Learn how environment separation safeguards confidentiality, integrity, and availability.
Innovation drives business but without clear boundaries, it can also drive risk.
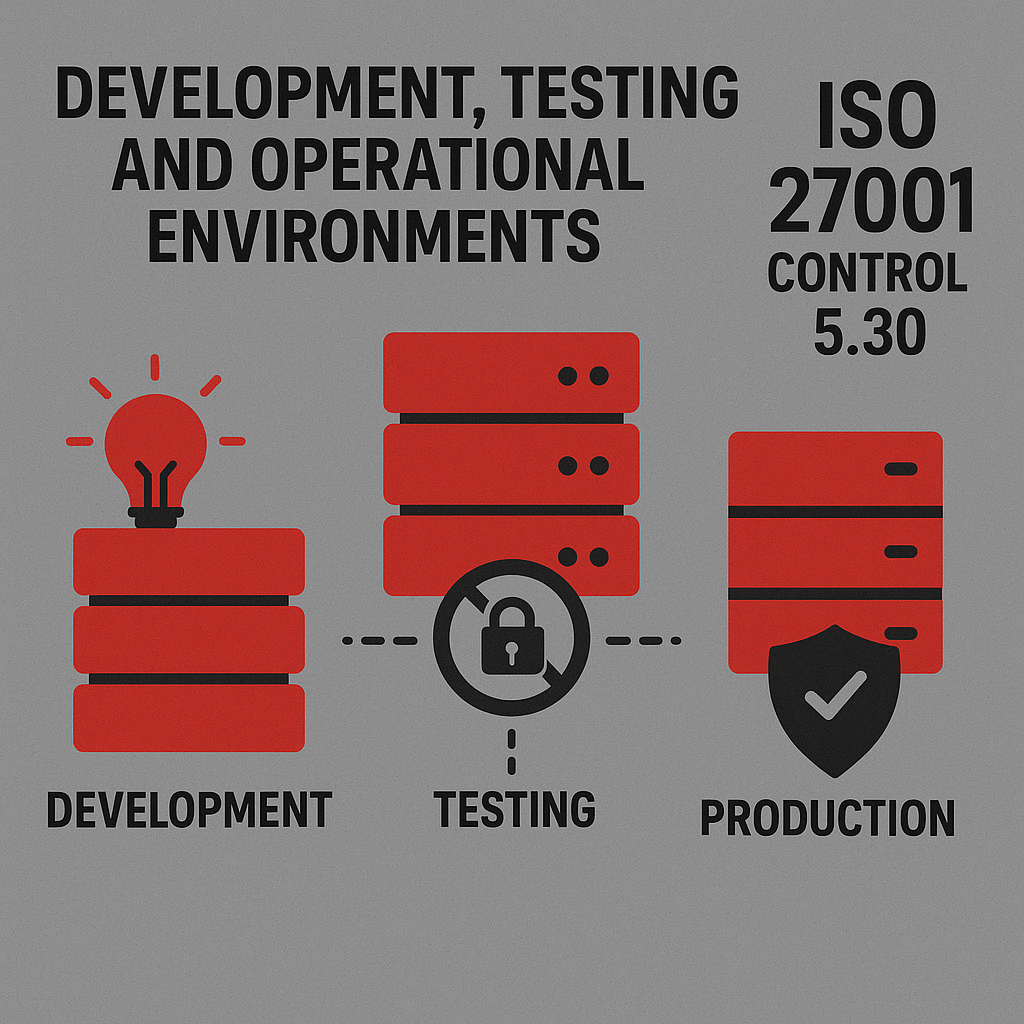
Developers and testers often need real data, live systems, and flexibility. But if development, testing, and production environments aren’t properly separated, a simple coding error or misconfiguration could compromise live systems.
ISO 27001 Control 5.30 Development, Testing, and Operational Environments ensures that innovation doesn’t come at the cost of security.
Picture this:
A developer tests a new application patch using the production database “just this once.”
The test goes wrong, wiping real customer data or exposing sensitive credentials.
This control, from ISO/IEC 27002:2022 Section 5.30, is an Organizational control that’s primarily preventive, supporting Confidentiality, Integrity, and Availability through the Protect concept.
In essence it ensures development and testing are safe playgrounds, while production stays stable, secure, and untouched by mistakes.
Physical and Logical Separation:
Use different servers, databases, and credentials for development, testing, and production.
Access Control:
Limit who can access production systems; developers should not have unrestricted production access.
Use of Sanitized Data:
Use anonymized or synthetic data in testing environments to prevent exposure of real customer information.
Configuration Management:
Implement strict change controls for promoting code between environments.
Monitoring and Logging:
Log access and activities across all environments to detect misuse or mistakes.
Periodic Reviews:
Regularly audit environment boundaries to ensure separation remains intact.
Test code accidentally deployed to production
Real customer data used in testing environments and leaked
Developers with unrestricted production access
Changes promoted without approval or rollback plans
At Canadian Cyber, we help organizations establish secure development and operational boundaries that align with ISO 27001 best practices.
We ensure your DevOps workflows maintain speed without compromising control, from environment setup to code deployment.
Our approach combines security-by-design principles with practical DevSecOps integration, making compliance a natural part of the process not a bottleneck.
Great development needs freedom but safe development needs boundaries.
ISO 27001 Control 5.30 keeps your creativity productive and your production environment protected.
Innovation shouldn’t come with risk it should come with resilience.
At Canadian Cyber, we provide:
* ISO 27001 Internal Audit Services to give you a fresh perspective on your ISMS
* Compliance Readiness Reviews for ISO 27001, SOC 2, and other frameworks
* Practical recommendations to close gaps quickly
We also bring our expertise from delivering SOC 2 consulting for fast-growing startups, where we’ve helped clients navigate gap assessments, implement safeguards, and achieve compliance while staying agile.
👉 Ready to strengthen your ISO 27001 program? Book a free consultation here.
🔗 Stay updated with the latest cybersecurity tips by following us on
LinkedIn, Instagram, Facebook, and YouTube.