Beyond the Badge
Why Continuous SOC 2 Compliance Matters More Than Passing the Audit
SOC 2 isn’t a once-a-year project. In 2026, buyers expect always-on controls, always-current evidence, and a program that runs quietly in the background.
Read time: 6–8 minutes
Keywords: continuous SOC 2 compliance, SOC 2 controls, SOC 2 evidence, SOC 2 Type II readiness, vCISO SOC 2, audit readiness
Passing SOC 2 once doesn’t protect you between audits.
Continuous compliance means controls run daily, reviews happen on schedule, and evidence is produced automatically so audits become routine.
For many companies, SOC 2 feels like a finish line.
The report arrives. The deal closes. The pressure disappears.
Until next year.
In 2026, that mindset gets companies burned:
customers and partners want continuous SOC 2 compliance, not last-minute heroics.
SOC 2 isn’t a badge. It’s an operating model.
The problem with treating SOC 2 as a one-time event
Organizations that treat SOC 2 like an annual project often run into the same issues:
- Scrambles before every audit
- Missing or outdated evidence
- Controls that look good on paper but fail in practice
- Findings that repeat year after year
Worse, many security gaps appear between audits not during them.
What “continuous SOC 2 compliance” really means
Continuous compliance means your controls:
- Operate every day
- Are reviewed on a schedule
- Produce evidence automatically
- Improve over time
When the auditor returns:
nothing feels rushed because nothing is new.
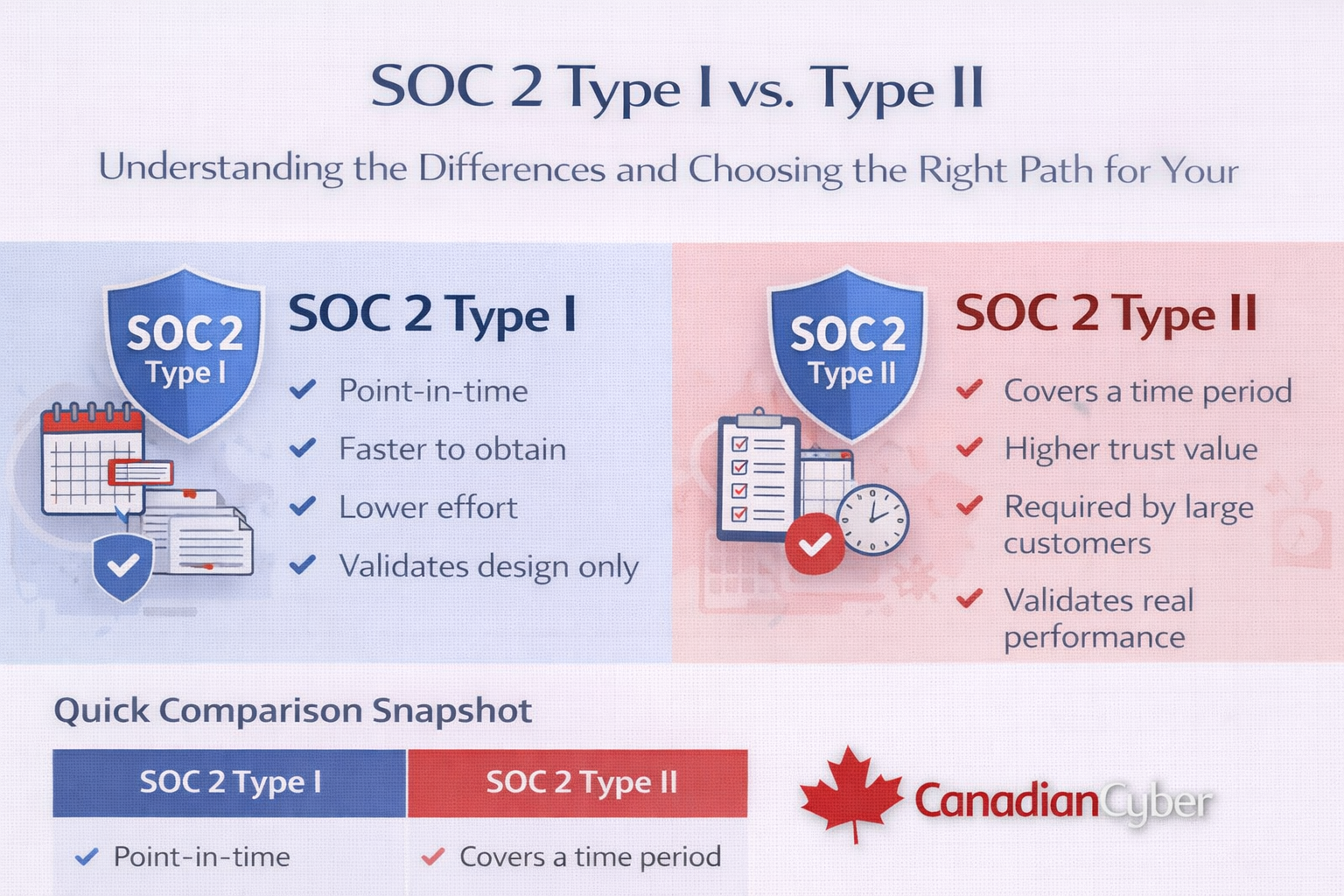
Quick snapshot: annual SOC 2 vs. continuous SOC 2
5 strategies that make SOC 2 continuous (not painful)
Strategy 1: Make access reviews routine, not reactive
User access is one of the most tested SOC 2 controls and one of the most commonly neglected.
Continuous compliance means access reviews are scheduled and repeatable.
- Monthly or quarterly access reviews
- Clear approval workflows
- Evidence stored centrally
Why it matters: privilege creep quietly increases risk and auditors spot it fast.
Strategy 2: Automate logging and alerts
Logs only help if someone is watching them. Mature SOC 2 programs use automation to reduce human error.
- Centralized logging for critical systems
- Automated alerts for high-risk events
- Documented log review routines
Strategy 3: Run quarterly risk assessments
Risk changes faster than annual audits. New vendors, new features, and new threats appear constantly.
- Identify emerging risks early
- Update controls proactively
- Show auditors a living risk program
This is the shift:
SOC 2 becomes strategic not administrative.
Want a “SOC 2 all-year” operating rhythm?
Get a simple cadence for access reviews, evidence capture, and quarterly risk checks so audits stop feeling like a crisis.
Strategy 4: Treat evidence as a byproduct of work
The best SOC 2 programs don’t “collect” evidence. They generate it naturally through daily workflows.
- Policies approved through workflows (with audit trails)
- Tickets showing control execution
- Logs captured automatically
- Reviews documented as part of operations
Strategy 5: Assign ongoing control ownership
Controls fail when no one owns them. Auditors look for consistency not perfection.
- Named control owners
- Defined review schedules
- Clear accountability across teams
The pattern Canadian Cyber sees in successful SOC 2 programs
Organizations that maintain SOC 2 year-round typically:
- Spend less time preparing for audits
- Have fewer findings
- Answer customer security questionnaires faster
- Build stronger trust with enterprise clients
SOC 2 becomes a business advantage not a burden.
How Canadian Cyber enables continuous SOC 2 compliance
Canadian Cyber helps teams move beyond audit panic by combining leadership with structure:
- vCISO leadership to keep controls owned and operating
- SOC 2 readiness + ongoing support (not just audit season help)
- SharePoint-based ISMS for policies, evidence, and workflows
The result: controls stay active, evidence stays current, and audits stay predictable.
Final takeaway
SOC 2 isn’t about passing an audit once.
It’s about proving every day that your security program works.
When compliance is continuous, audits become routine.
And trust becomes effortless.
Build SOC 2 that lasts all year
Replace annual fire drills with a calm, repeatable program that customers trust and teams can maintain.
Stay Connected With Canadian Cyber
Follow us for real-world insights on SOC 2, continuous compliance, vCISO leadership, and audit readiness: