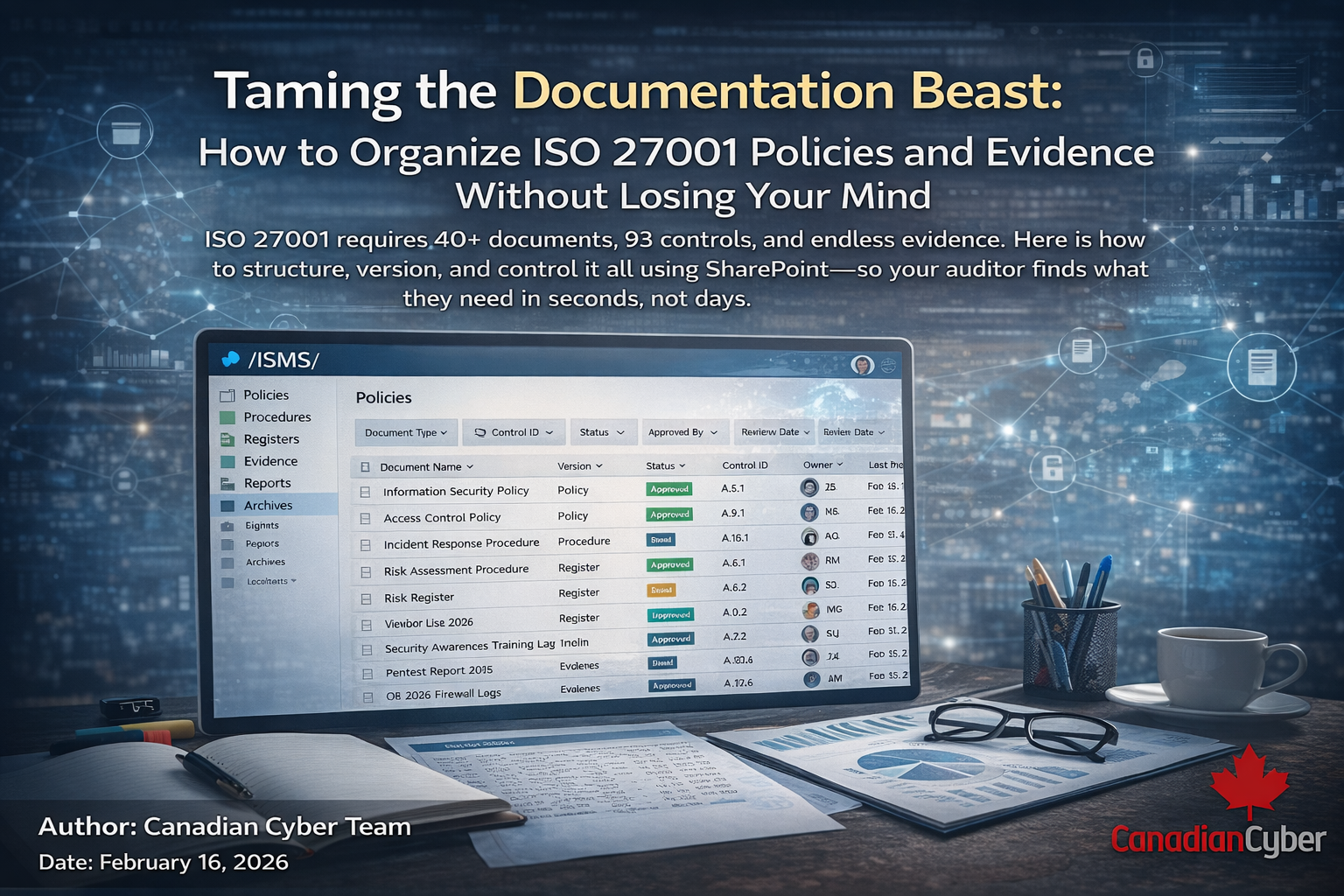
Introduction
In today’s data-driven world, every organization wants to analyze and innovate but not at the cost of privacy.
That’s where ISO 27001 Control 5.50 Data Masking comes in. It helps organizations protect sensitive information while still allowing data to be used safely for testing, development, and analytics.
Because in cybersecurity, protecting data doesn’t mean locking it away it means making it safely usable.
What Is Data Masking?
Data masking is the process of replacing real data with fictitious but realistic values. The goal? To make the data unusable to attackers while still useful for legitimate business activities.
For example:
- Real customer names → replaced with fake ones
- Credit card numbers → replaced with random numbers
- Personal details → anonymized or tokenized
It’s especially useful when organizations need to share or process data without revealing sensitive information.
Why ISO 27001 Control 5.50 Matters
Even the most secure organizations sometimes mishandle test or development data. Developers or third parties often use real production data to test systems unintentionally exposing private information.
ISO 27001 Control 5.50, from ISO/IEC 27002:2022 Section 5.50, is a Technical and Organizational control designed to:
- ✅ Protect sensitive data from unauthorized access
- ✅ Reduce the impact of data breaches
- ✅ Enable safe use of data in non-production environments
- ✅ Support privacy regulations like GDPR, PIPEDA, and ISO 27018
It supports the security principles of Confidentiality and Integrity, following the cybersecurity concepts of Protect and Minimize.
How to Implement Data Masking
Here’s how organizations can apply Control 5.50 effectively:
- Identify Sensitive Data: Locate personal, financial, or health data across your systems.
- Select Appropriate Masking Techniques: Use methods like substitution, shuffling, tokenization, or encryption depending on your needs.
- Apply Masking in Non-Production Environments: Never use real customer or employee data in development or testing.
- Secure Access to Unmasked Data: Limit the ability to reverse or unmask data to only authorized users.
- Automate Masking Workflows: Use tools like Microsoft Purview, Azure Data Masking, or Power BI governance to standardize the process.
Common Mistakes in Data Masking
- 🚫 Using real customer data for testing or QA
- 🚫 Inconsistent masking rules across databases
- 🚫 Reversible masking techniques without proper control
- 🚫 Neglecting third-party or API-level data exposure
These mistakes can undo the very protection data masking provides leaving you vulnerable to breaches and compliance risks.
Canadian Cyber’s Take
At Canadian Cyber, we help organizations design and implement data masking frameworks that align with ISO 27001, ISO 27018 (Cloud Privacy), and global data protection standards.
We integrate masking and tokenization into your existing platforms from Microsoft 365 and Azure to Power BI and SQL ensuring sensitive data remains protected no matter where it lives.
Our focus:
- 🔹 Keep your data useful
- 🔹 Keep your privacy intact
- 🔹 Keep your compliance effortless
Because smart masking means your teams can innovate securely without putting data at risk.
Key Takeaway
ISO 27001 Control 5.50 Data Masking ensures sensitive information is protected while still supporting real-world business needs.
It’s a bridge between data security and data usability a way to empower innovation without compromising privacy.
If your test data looks real, it should still be fake. That’s true protection.
How Canadian Cyber Can Help
- Data Masking and Tokenization Implementation (Microsoft Purview, Azure)
- ISO 27001 & ISO 27018 Privacy Consulting
- Information Security Management and Internal Audit Services
👉 Ready to make your data safe and compliant? Book a free consultation here.