SOC 2 Type I vs. Type II
Understanding the Differences and Choosing the Right Path for Your Company
If you’re new to SOC 2, this question comes up fast often after a deal slows down:
Do we need SOC 2 Type I or Type II? This guide breaks it down in plain language so you can choose the right path with confidence.
Read time: 6–8 minutes
Keywords: SOC 2 Type I, SOC 2 Type II, SOC 2 readiness, Trust Services Criteria, SaaS compliance, vendor due diligence
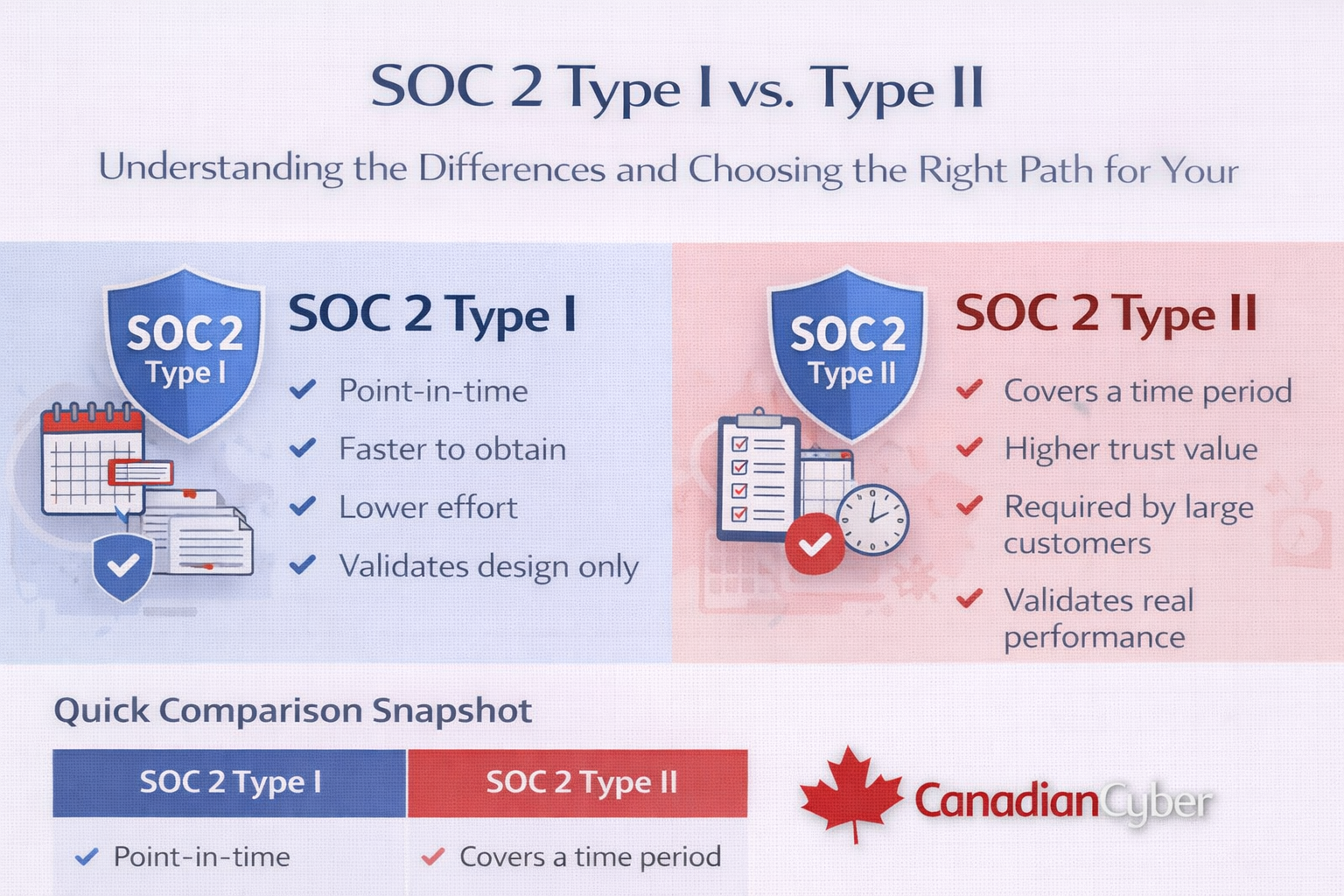
Type I proves your controls are designed correctly on a specific date.
Type II proves your controls work consistently over time (usually 3–12 months).
Most companies start with Type I, then move to Type II for enterprise trust.
Why this question shows up under pressure
SOC 2 often enters the conversation when something important is already happening:
a customer asks for a report, a deal stalls, or an enterprise buyer starts due diligence.
- A customer asks for a SOC 2 report
- A deal slows down during security review
- A bank, enterprise, or partner raises concerns
Good news:
Type I and Type II aren’t competing options. They’re usually two steps of the same journey.
What is SOC 2 (in simple terms)?
SOC 2 is an independent assurance report that shows how your organization protects customer data.
It is built around the Trust Services Criteria, most commonly:
- Security (most common)
- Availability
- Confidentiality
- Processing Integrity
- Privacy (optional, based on scope)
SOC 2 is especially common for SaaS, FinTech, cloud, and technology companies that need to prove trust to customers.
The core difference: Type I vs. Type II
Both reports evaluate controls. The difference is what the auditor is verifying.
Type I is a snapshot. Type II is proof over time.
Quick comparison snapshot
SOC 2 Type I: a point-in-time snapshot
Type I shows your controls are designed correctly on a specific date.
Think of it as answering:
“Do the right controls exist today?”
Best for:
- Early-stage startups
- First-time SOC 2 candidates
- Companies needing faster proof for customers
Practical note: Type I is often the starting point, not the destination.
SOC 2 Type II: proof over time
Type II shows your controls are designed and operating effectively over a defined period (often 3–12 months).
It answers:
“Do these controls actually work consistently?”
Best for:
- Scaling companies
- Enterprise SaaS vendors
- FinTech and regulated industries
- Organizations selling to banks and large partners
Bottom line:
Type II is the gold standard most enterprises and banks expect.
Which one should you choose first?
For most companies, the best approach is a smart progression.
Start with Type I to establish the foundation, then move to Type II to scale trust.
A common mistake startups make
Some startups rush straight into Type II.
If controls aren’t stable, the audit period becomes stressful and expensive.
A safer progression:
- Complete Type I
- Fix gaps early
- Operate controls consistently
- Achieve Type II confidently
Why it matters:
Fixing issues mid-audit is slower, more costly, and disrupts teams.
How preparation changes everything
SOC 2 success is mostly readiness not the audit itself.
Companies that move faster and cleaner usually do four things:
- Run a readiness assessment before auditors arrive
- Centralize policies and evidence in one place
- Assign clear control ownership (no “someone should do this”)
- Track controls continuously, not at the last minute
Not sure if you’re Type I-ready or Type II-ready?
Get clarity on gaps, scope, and the fastest path to the report your buyers will accept.
How Canadian Cyber helps you choose the right path
Canadian Cyber supports organizations at every SOC 2 stage—from first-time readiness to enterprise-level Type II.
Our vCISO-led approach keeps SOC 2 practical and business-aligned.
- Decide between Type I and Type II based on your buyers and timelines
- Prepare controls the right way to avoid rework
- Reduce audit delays with structured evidence and ownership
- Align SOC 2 with ISO 27001 when it makes sense
Final takeaway
SOC 2 Type I and Type II are not competing options.
They are steps on the same journey.
Choose the right step for today, then build toward Type II trust at scale.
With the right readiness plan, SOC 2 becomes a growth enabler not a blocker.
Next step:
Start smart, build trust, and scale confidently with a SOC 2 plan that matches your stage.
Want SOC 2 to move deals forward faster?
Get a clear scope, clean evidence, and a readiness plan built for your customers’ expectations.
Stay Connected With Canadian Cyber
Follow us for practical insights on SOC 2, ISO 27001, vCISO leadership, and compliance strategy: